Définition
DNS over HTTPS est un protocole permettant d’effectuer une
résolution DNS à distance via le protocole HTTPS.
Voici une implémentation afin d’autohéberger un service DNS Over HTTPS.
Fonctionnement (simplifié)
+------------+ (requete dns overhttps) +-------------+
| navigateur | ------------------------> | nginx https |
+------------+ +-------------+
|
| (requete doh-server)
|
+-------------+
| doh-server |
+-------------+
|
| (requete dns)
|
+------------+
| Server DNS |
+------------+
Installation: Ubuntu 16.04
Pour Debian, Centos, Ubuntu>16.04 ou autre, la démarche est la même.
Il faut télécharger et installer
doh-server
ou le compiler: github.
dpkg -i doh-server_2.0.1_amd64.deb
Configuration du server doh-server:
upstream: vos serveurs DNS (bind ou autre), ici ce sont les 2
ips opendns.verbose: Mettre a true pour debugger dans syslog
(sinon remettre à false)- On bind le service sur le l’ip privé de mon serveur 192.168.10.4
- Le certificat est généré en amont sur le reverse proxy
root@ubuntu:/etc/dns-over-https# more doh-server.conf
# HTTP listen port
listen : [
"127.0.0.1:8053",
"[::1]:8053",
"192.168.10.4:8053",
]
# TLS certification file
# If left empty, plain-text HTTP will be used.
# You are recommended to leave empty and to use a server load balancer (e.g.
# Caddy, Nginx) and set up TLS there, because this program does not do OCSP
# Stapling, which is necessary for client bootstrapping in a network
# environment with completely no traditional DNS service.
cert : ""
# TLS private key file
key : ""
# HTTP path for resolve application
path : "/dns-query"
# Upstream DNS resolver
# If multiple servers are specified, a random one will be chosen each time.
#upstream : [
# "1.1.1.1:53",
# "1.0.0.1:53",
# "8.8.8.8:53",
# "8.8.4.4:53",
#]
upstream : [
"208.67.222.222:53",
"208.67.220.220:53",
]
# Upstream timeout
timeout : 10
# Number of tries if upstream DNS fails
tries : 3
# Only use TCP for DNS query
#tcp_only : false
tcp_only : false
# Enable logging
#verbose : false
verbose : true
# Enable log IP from HTTPS-reverse proxy header: X-Forwarded-For or X-Real-IP
# Note: http uri/useragent log cannot be controlled by this config
log_guessed_client_ip : true
- On ajoute le service au démarrage de la machine et on le démarre
systemctl enable doh-server
systemctl restart doh-server
Configuration NGINX en frontale
- Création d’un fichier de conf pour la configuration du site
https://mondnsoverhttps.fr - Ajout d’un auth_basic pour ne pas laisser mon dns ouvert à tous.
upstream dns-backend {
server 192.168.10.4:8053;
}
server {
listen 443 ssl http2;
server_name mondnsoverhttps.fr;
access_log /var/log/nginx/mondnsoverhttps.fr.log combined;
location /dns-query {
auth_basic "niet";
auth_basic_user_file /etc/nginx/passwd;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
proxy_set_header X-NginX-Proxy true;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_redirect off;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_read_timeout 86400;
proxy_pass http://dns-backend/dns-query ;
}
...
Configuration du navigateur
Dans Préférences/Paramètres de connexion de Firefox.
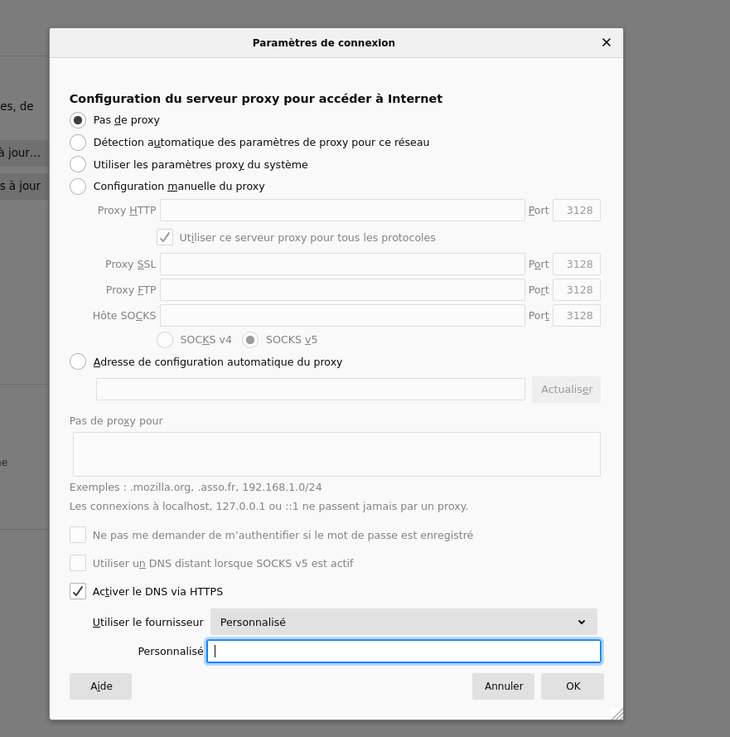
Ajoutez https://login:mdp@mondnsoverhttps.fr/dns-query
Test et Debug
- lors d’une requête DNS du navigateur:
root@ubuntu:/etc/dns-over-https# tcpdump host 208.67.222.222
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
13:10:15.198973 IP 192.168.10.4.49917 > resolver1.opendns.com.domain: 22816+ [1au] A? www.google.com. (51)
13:10:15.220176 IP resolver1.opendns.com.domain > 192.168.10.4.49917: 22816 1/0/1 A 216.58.204.100 (59)
13:10:16.429722 IP 192.168.10.4.54204 > resolver1.opendns.com.domain: 6866+ [1au] A? linuxfr.org. (48)
13:10:16.530155 IP resolver1.opendns.com.domain > 192.168.10.4.54204: 6866 1/0/1 A 88.191.250.176 (56)
13:10:16.611363 IP 192.168.10.4.36449 > resolver1.opendns.com.domain: 23736+ [1au] A? ocsp.int-x3.letsencrypt.org. (64)
13:10:16.700923 IP resolver1.opendns.com.domain > 192.168.10.4.36449: 23736 4/0/1 CNAME ocsp.int-
x3.letsencrypt.org.edgesuite.net., CNAME a771.dscq.akamai.net., A 104.123.50.43, A 104.123.50.123 (174)
13:10:16.740028 IP 192.168.10.4.57706 > resolver1.opendns.com.domain: 50387+ [1au] A? ocsp.int-x3.letsencrypt.org.edgesuite.net. (78)
13:10:16.823159 IP resolver1.opendns.com.domain > 192.168.10.4.57706: 50387 3/0/1 CNAME a771.dscq.akamai.net., A 104.123.50.43, A 104.123.50.123 (133)
13:10:17.239958 IP 192.168.10.4.56057 > resolver1.opendns.com.domain: 25580+ [1au] A? img.linuxfr.org. (52)
13:10:17.314693 IP resolver1.opendns.com.domain > 192.168.10.4.56057: 25580 2/0/1 CNAME prod.linuxfr.org., A 88.191.250.176 (79)
- Log NGINX:
[09/Dec/2019:13:48:01 +0100] "POST /dns-query HTTP/2.0" 200 63 "-" "Mozilla/5.0 (X11; Linux x86_64; rv:71.0) Gecko/20100101 Firefox/71.0"
Un petit pas supplémentaire pour la confidentialité de vos navigation web.
Biz